Supermicro and Facebook follow-up, Dutch GRU operation, and Derbycon talks
Good morning.
What a week. It’s becoming difficult to make these weekly summaries, because there’s just so much going on in the security world these days.
Case in point: I was almost finished drafting this email when a new Bloomberg story dropped, this time alleging that Supermicro servers at a “major U.S. telecommunications company” were discovered with hardware implants built into ethernet ports. The story is again short on technical detail, but this time names a source: Yossi Appleboum from Sepio Systems.
This story is ‘developing’, so stay tuned. In the meantime, Motherboard has a good summary of everything here, including the fact that no one really knows what to believe at this point.
Follow-up: Supermicro, hardware trojans, and BMC security
Since Monday’s post there have been some more developments in the original Supermicro hardware trojan story - the one which implicated servers at Apple and Amazon.
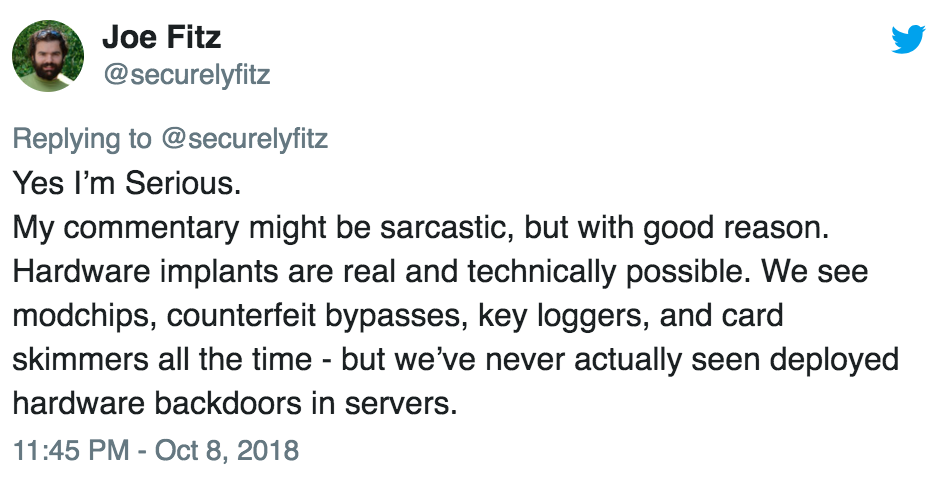
First up: Patrick Gray recorded another podcast episode where he interviewed Joe Fitzpatrick, one of the few named sources in the original Bloomberg article. If you don’t have time to listen to the episode, Apple Insider has a good summary here.
Since the original story broke, Fitzpatrick has also written some excellent Twitter threads on hardware implants generally. One example (from the end of the thread):
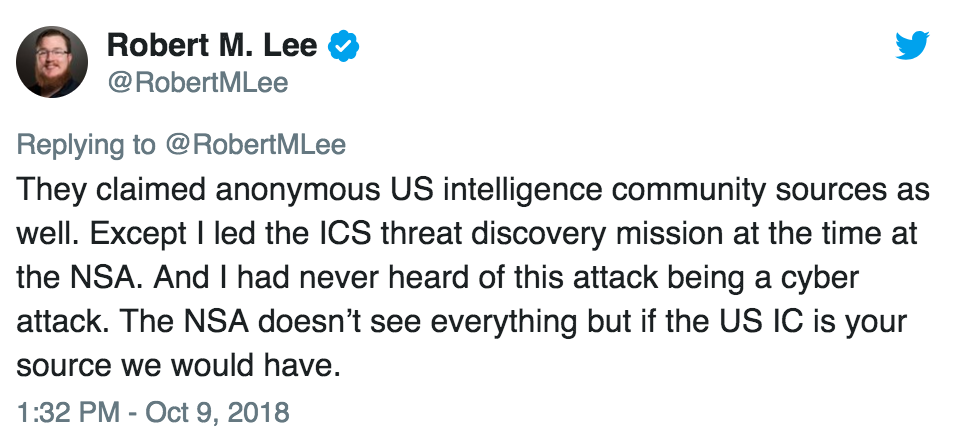
Former NSA member Robert M. Lee also weighed in regarding a previous Bloomberg story authored by the same journalists, which claimed that a pipeline explosion in Turkey was a Russian cyber attack:
In both cases, it’s worth reading the full thread.
And finally, Brian Krebs has written an excellent blog post about the Supermicro hardware trojan story and supply-chain security more generally:
Like it or not, the vast majority of electronics are made in China, and this is unlikely to change anytime soon. The central issue is that we don’t have any other choice right now. The reason is that by nearly all accounts it would be punishingly expensive to replicate that manufacturing process here in the United States.
Facebook follow-up: third-party website SSO implementations
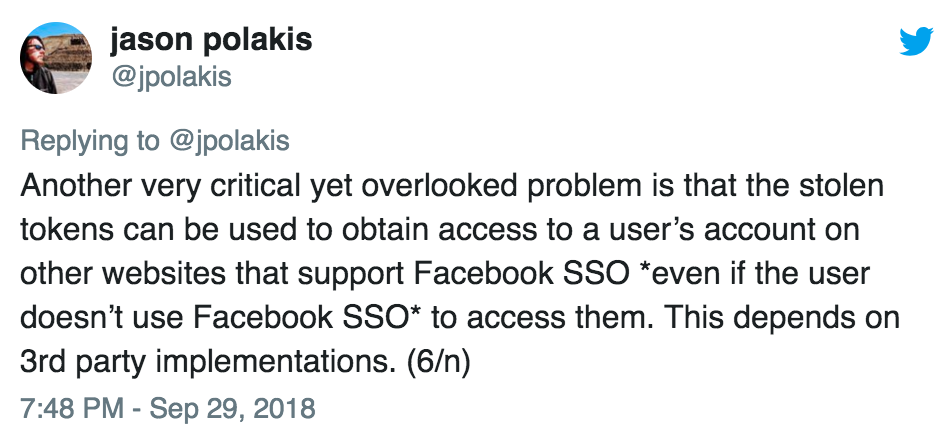
Some follow-up to my Facebook post from last week, via Jason Polakis:
I’d highly recommend reading the whole thread, but to rephrase this part: if a third-party service you use (like Tinder or Airbnb) has integrated with Facebook Login to allow single-sign-on (SSO), but you personally don’t use this functionality, it may still be possible for an attacker who has a copy of your Facebook user access token to log into the third-party service as you.
Think of it this way: depending on how the site has implemented Facebook’s SSO, giving them a stolen Facebook token which matches your email address might pass their user authentication code, telling the back-end of the service “yep, this is a valid login for jane.doe@gmail.com”. Depending on how the service is written, this could be possible even if Jane Doe doesn’t actually use Facebook SSO for that service.
The implication of this is that if Facebook allows an attacker to steal 50 million user access tokens, the number of affected accounts across all services which integrate with Facebook Login starts getting very large - and as it stands, users aren’t really aware of the risk this poses.
Polakis knows his stuff when it comes to Facebook SSO: he co-authored a paper on the implications of compromised Facebook accounts which was accepted at USENIX 2018.
Dutch intelligence breaks up GRU cyber operation
In any normal news week this would have been the leading story. From Business Insider:
Four Russian intelligence agents were caught trying to hack the global chemical weapons watchdog while it was investigating their country, Dutch authorities said on Thursday.
The suspects traveled to the Netherlands this April to try to launch a cyberattack on Organisation for the Prohibition of Chemical Weapons, which is headquartered in The Hague, the head of Dutch military intelligence said in a press conference.
Major General Onno Eichelsheim said the OPCW was at the time investigating the nerve agent poisoning of former Russian spy Sergei Skripal in England, as well as a chemical attack on Douma, Syria.
There’s also this Twitter thread by Gordon Corera, which has some more technical detail about what the Russians were doing.
In addition, in the process of confirming the identities of the arrested agents, investigative news site Bellingcat was able to identify over 300 other potential GRU agents from a public Russian car registration database. Whoops.
Derbycon 2018 Presentations
The Derbycon security conference recently wrapped up in the U.S., and there are some fantastic presentations I’d highly recommend watching if you have time:
- The Unintended Risks of Trusting Active Directory (SpecterOps: Lee Christensen, Will Schroeder, and Matt Nelson)
- From Workstation to Domain Admin: Why Secure Administration Isn’t Secure and How to Fix It (Sean Metcalf of ADSecurity.org)
- The MS Office Magic Show (Stan Hegt, Pieter Ceelen)
I’m still working my way through the other talks, so to save me some time - if you have any personal favourites, please let me know!